Quest of Kings
Canada
Independently developed and published as freeware
Released in 1990 for Commodore 64
Date Started: 15 September 2020
Date Ended: 20 September 2020
Total Hours: 9
Difficulty: Moderate (3/5)
Final Rating: (to come later)
Ranking at Time of Posting: (to come later)
For fans and bloggers of computer role-playing games, there are few resources on the web that are more important--more awesome--than the Museum of Computer Adventure Game History. Since 2001, creator Dr. Howard Feldman, a Toronto biochemist, has provided high-quality scans of the boxes, disks, manuals, clue books, maps, and accompaniments to thousands of computer adventure and role-playing games, most of them curated not from other sites but from scans that Feldman has made of the items in his physical collection. He also has complete sets of gaming magazines, newsletters, and hint books. The brick-and-mortar "museum" is not open to the public, but once I'm allowed to travel to Canada again, I would love to visit Dr. Feldman some day in Toronto and see some of his treasures in person. He has an original copy of Akalabeth donated by Richard Garriott himself.
What is less well known about Dr. Feldman is that while he was still a high school student, he wrote two freeware computer RPGs: Quest of Kings for the C64 in 1990 and The Search for Freedom for the PC in 1994. Neither is going to be "Game of the Year," but they're both reasonably fun freeware games, and the young Feldman notably did all the programming, graphics, and sound effects himself. The game uses Dungeons and Dragons conventions and plays a bit like a small D&D module.
 |
| Exploring the hallways of the dungeon. The compass doesn't appear until you find and equip a compass. |
Quest of Kings takes place in the land of Kwantulaursia (whoa), where peace was kept for centuries by the custom of simply obeying whoever wore the magical Crown of Kingship. But, as often happens in such stable societies, a necromancer called the Evil One decided to take the crown for himself. He raised an army of beasts, orcs, and undead, and stole the crown from good King Cersis VI, leaving the land in chaos. Figuring that one agent is less conspicuous than an entire army, king's men have been putting posters in local taverns. The PC sees one, grabs a dagger, gets some advice from a wizard named Bagle, and assails the Evil One's lair.
A couple of bars of Bach's Toccata and Fugue in D Minor play over the title screen, and then we get a little of Grieg's "In the Hall of the Mountain King" as the game loads. Character creation consists of random rolls for to-hit score, maximum hit points, dexterity, strength, and armor, then a name. Soon, the character is at 0,0 on Level 1. Except for a few places in which you have to enter text, the joystick controls all the action. Even visiting inventory requires pushing down and the button at the same time.
The dungeon consists of four 16 x 16 levels. There are no open areas--every square is its own room or section of a corridor--so it took me a while to map. There are the usual tricks like teleporters, secret doors (identifiable by a small mark in the lower-right corner), and one-way doors. Levels 1, 2, and 3 are connected by multiple staircases, but there's only one heading down to Level 4.
Encounters come along every 10-12 steps, roughly. Each level has its own set of foes. After an initial screen in which the player can fight or flee (fleeing works about 80% of the time), his options are attack, defend, or visit his inventory to use an item. Enemies only attack; none of them have magical abilities or special attacks, not even those that you would expect, like ghouls and snakes. Combats can take a long time, particularly if you're attacked by a group with lots of foes, and I was appreciative of VICE's "warp" mode to get through most of them.
The major downside of the game is that there's no experience and no leveling. Whatever you started with in terms of maximum health and other attributes, you're mostly stuck with. The only way to get stronger is to find better items at the end of combat. (Items are never found outside of combat.) Since you have an equal likelihood of finding something useful whether you fought 6 orcs or just one, it's best to flee combats with large parties.
Inventory items get progressively better on lower levels. They include armor, weapons, shields, helms, bracers, gauntlets, and occasional magical items like Wands of Magic Missile, Wands of Fireball, and Scrolls of Death. Most important are healing ointments and potions; if you don't find any of these, you can't heal. Healing items can only be used outside of combat, which causes some problems late in the game when you face large parties of very hard enemies. A high maximum hit point during character creation is a must.
 |
| My inventory late on Level 2. |
Level 1's enemies include orcs, kobolds, pygmies, and goblins. With luck, you can find a long sword, a shield, scale armor, and maybe a Wand of Magic Missiles before heading downward. Level 2 has ghouls, skeletons, and minotaurs, and you start to see the first magic items, like short swords +1. Level 3 really kicks it up a notch in enemy difficulty with robotic clones, red dragons, crystal warriors, trolls, and king cobras, but you get even better equipment, including some +2 items. Level 4 features vampire lords, werewolves, war giants, manticores, and dragon kings; here, you can find Gloves of Strength and Helms of Dexterity (both raise their attributes to 18), Bracers AC4, and +4 weapons and shields. There are also high-level magic items to use, such as Scrolls of Death and grenades. The trick is to not go to the next level until you have the best stuff from the current one.
The lack of character development otherwise would make for a relatively boring game except for Quest's use of special encounters and riddles. Each level has a few "boss" creatures, usually guarding a room with a key piece of intelligence. On Level 1, for instance, a magic mouth says, "He had vowed no mortal brave would take him to his very ________." A little thought to the rhyme reveals the answer as GRAVE. At this, the mouth says, "Until he came along to prove him wrong. A man known as Sir Dave!" This isn't just doggerel. On level 2, you have to give Dave's name, as well as his hometown, to open the doorway to the stairs to Level 3. You also have to slay a red dragon to get into this area.
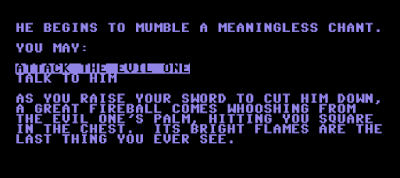
Level 4 ultimately brings you face to face with The Evil One, and to defeat him, you have to have been paying attention to several clues. If you just attack him, he immediately kills you with a fireball. Instead, you have to choose the "Talk to him" option.
Previously, a clue has alerted you that you can "speak the four-letter word to bring the evil one to your mercy." You have also seen a bunch of "jibberish" on a wall that reads: "FTRAX FROJ HBL BNL OV EYTNANM WIPFL OSK IQUG." I thought at first that this was a cryptogram, but no solution made any sense. I then realized you have to look at it along with a clue from a magic mouth on Level 2: "Search with all your 'heart' on the level below for the word you seek." The nonsense text string has LOVE embedded within it, which is what you have to say to the Evil One.
In disgust, the Evil One flees, leaving you to content with three war giants followed immediately by six shadow lords with no way to heal in between. There is no way to win this battle through conventional attacks. You have to have at least a few high-damage magic items. I had to reload and grind a bit until I had a Scroll of Death and a couple of grenades. These together let me kill the two parties before I ran out of hit points.
After this battle, you'd better have a healing potion, because you then have to fight another double header. The first is against the Evil One, who cannot use magic because of your repetition of LOVE, but can still use physical attacks. He's not too hard, but just as he dies, he casts a spell that replicates you and forces you to fight against a shadow of yourself. This battle is a little harder.
Once the battles are done, you still have to find your way to the central chamber of the level and the Crown of Kings. Outside, a magic mouth says that you have to give it two words. Again, you have to interpret a couple of clues that you found in other rooms:
- "It is to be supposed that the first isn't closed."
- "After all else had failed, he was left with no choice but to ask politely."
 |
| The mouth did not like my first attempt at a two-word phrase. |
Together, these reveal that the phrase is OPEN PLEASE. It took me a long time, particularly because I hadn't encountered the first message on my first pass through the area.
After this, you can enter and pick up the Crown of Kings, which makes you the king. Your inventory screen even changes to put "King" before your name.
Unfortunately, this is where things fell apart for me. The game says that you have to find your way to the surface, but I can't figure out how to do that. The down ladder from Level 3 to Level 4 is on the other side of a one-way door, so there's no way to get back to the rest of Level 3. I searched every square of Level 4 and didn't find an alternate ladder or teleporter. I tried using all my times as well as fighting random battles to see if the enemies dropped a Scroll of Teleport or something. No luck. I even tried letting myself get killed, but that just resulted in the "game over" screen. Dr. Feldman didn't remember, either. It's possible that it's a bug and no one ever made it this far before; the only way to be sure would be to search the source code, which you're welcome to do at the link below.
 |
| Chester is king. I'm going to consider this "won." |
A search of text in the game file suggests that you are supposed to make it to the exit and that when you arrive, the ghost of the Evil One appears to vow revenge just before the entire dungeon collapses. Back in town, the Kwantulaursians proclaim you their king, throw a party, and end the game with a toast to your health. However, the game notes ominously that there is an "unwelcome guest" within the crowd.
Aside from the riddles, which were fun and occasionally challenging, it's a fairly basic game, but I'm not going to criticize something that a 10th-grader created as freeware. It earns a 17 on my GIMLET, doing best in "encounters" and "gameplay" (both 3s), the latter primarily for its moderate difficulty and length. Four dungeon levels is an ideal size for a game of limited content. It gets hurt in its lack of NPCs and economy. The monster graphics are worth a note. Although clearly the product of an amateur designer, they have a certain goofy earnestness about them, and it's hard not to be a little fond of them.
I wrote to Dr. Feldman to ask him a few questions about the game, and he was kind enough to supply his original notes, maps, and code, which he said I was welcome to share, so feel free to download and review it. I can interpret a little, but I'm not sure I see anything that would have been triggered by the final encounters and changes the layout of the dungeon.
Feldman started creating a Quest for Kings II the following year but never finished it. It somehow got out, and some sites offer it for download, but all you can do is create a party and look at the backstory. It would have been a more ambitious game, with a four-character party composed of the standard D&D races, classes, and attributes, except for a race called "Teddy" where you would expect to see a hobbit. The party is expected to stop the return of an evil archmage named Kamazol, one slain but now returned as a lich, but first they have to free themselves from a local jail. Many of the plot elements and mechanics made their way to Feldman's The Search for Freedom (1994) for DOS, which he finished around the end of his last year in high school. Feldman still sells Search as shareware on his web site; I look forward to playing it eventually. It promises to blend Ultima-style world exploration with Pool of Radiance-style combat.
I'll be visiting the Museum less and less in coming years. Although the site has some games that stretch into the mid-1990s, Feldman says that he's generally only interested in titles from 1992 and earlier. This blog would have been a poorer place if not for his images and documentation, and we all owe him a debt of gratitude for his work as an RPG creator and curator.