Let's implement a simple code that loads a file into a vector and then save the vector with following functions:
- err
- load
- save
- main
Lets identify the typical way in C++ to print to stdout with the operator "<<"
The basic_ostream is initialized writing the word "error" to the cout, and then the operator<< again to add the endl.
The Main function simply calls "vec = load(filename)" but the compiler modified it and passed the vector pointer as a parámeter. Then it bulds and prints "loaded " << size << " users".
And finally saves the vector to /tmp/pwd and print "saved".
Most of the mess is basically the operator "<<" to concat and print values.
Also note that the vectors and strings are automatically deallocated when exit the function.
And here is the code:
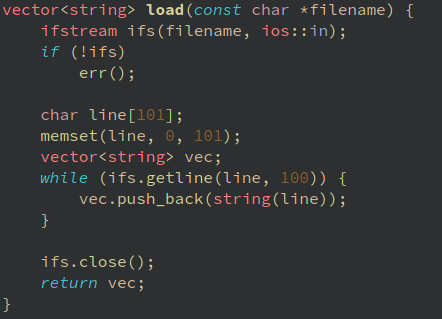
Let's take a look to the load function, which iterates the ifs.getline() and push to the vector.
First of all there is a mess on the function definition, __return_storage_ptr is the vector.
the ifstream object ifs is initialized as a basic_ifstream and then operator! checks if it wasn't possible to open the file and in that case calls err()
We see the memset and a loop, getline read a cstr like line from the file, and then is converted to a string before pushing it to the vector. lVar1 is the stack canary value.
The function save is a bit more tricky, but it's no more than a vector iteration and ofs writing.
Looping a simple "for (auto s : *vec)" in the decompiler is quite dense, but we can see clearly two write, the second write DAT_0010400b is a "\n"
More info
- Black Hat Hacker Tools
- Pentest Tools Online
- Hacker Tools Software
- Hacking Tools Pc
- Pentest Tools Website
- Hacking Tools
- Pentest Tools Url Fuzzer
- Hacker Tools Software
- Pentest Tools Apk
- Hacker Tools For Windows
- Hacking Tools For Windows Free Download
- Hacking Tools For Kali Linux
- Hack Tools Github
- Pentest Tools Url Fuzzer
- Pentest Tools Review
- Tools For Hacker
- Top Pentest Tools
- Hacker Tools
- Hacking Tools Hardware
- Pentest Recon Tools
- Pentest Tools Linux
- How To Install Pentest Tools In Ubuntu
- Bluetooth Hacking Tools Kali
- What Is Hacking Tools
- Termux Hacking Tools 2019
- Hacker Tools Online
- Hacking Tools For Games
- Pentest Tools
- Pentest Tools Github
- Hack Tools
- Pentest Tools Kali Linux
- Hacking Tools Pc
- Pentest Tools Subdomain
- Hacking Tools For Beginners
- Hack Tool Apk
- Blackhat Hacker Tools
- Hacking Tools For Kali Linux
- Hacking Tools For Windows
- Hack Tools For Ubuntu
- Hacking Tools For Beginners
- Pentest Tools Free
- Wifi Hacker Tools For Windows
- Pentest Tools Website Vulnerability
- Hacking Tools Download
- Hacker Tools Online
- Hack Tools Pc
- Hacking Tools Github
- Pentest Tools Tcp Port Scanner
- Hacker Tools 2020
- Black Hat Hacker Tools
- Hacker Tools Github
- Hacker Tools For Ios
- Top Pentest Tools
- Pentest Tools Framework
- Underground Hacker Sites
- Pentest Tools List
- Hacker Tool Kit








No hay comentarios:
Publicar un comentario